Simpler !!
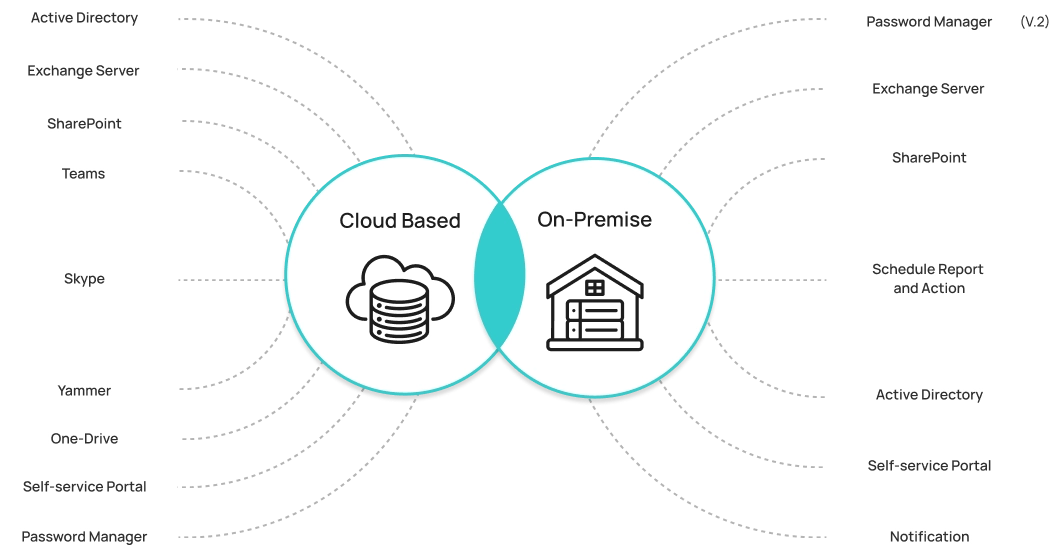
Exchange Server, and SharePoint. Try it now with our 14-day trial!








Management

Manager

Management
Portal
Compliance
and Automation
Administration
Management

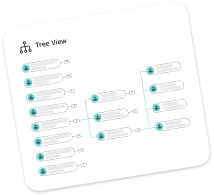
Asign2 offers an easily understandable and self-intuitive interface suitable for all administrative users (Novice and professionals). All your IT tasks can now be managed with focus and clarity.

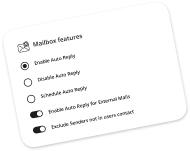
With Asign2, user management bypasses all the complexities as it gives seamless options for action-oriented tasks and report generation. Spend more time on more important things.

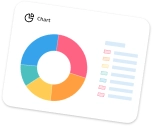
With Asign2, generating comprehensive reports becomes a breeze. Analyze and generate over 200 reports in 20 different formats, covering a wide range of report formats.

You can never miss out on important notifications or related time-bound actions. Stay ahead of the game on critical actions such as security breaches, system failures, or authentication issues.
Turn all your complex administrative tasks into a simple logic-based workflow and generate reports with ease. Get our 3-in-1
solution (AD Management, Exchange Server, and SharePoint) now and make your IT tasks smooth and efficient.





